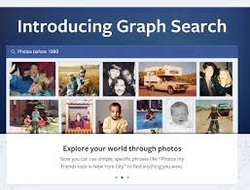
"...The Graph Search bar on Facebook has replaced my old search bar and now occupies a prominent place on the top tab of my Facebook homepage; the notifications, messages, friend requests tab are now on the right. The new design is giving Graph Search a lot more prominence and I’m not surprised, given Zuckerberg has called this the third pillar of the site at the launch . ." http://www.firstpost.com/tech/review-facebooks-graph-search-is-stalker-gold-605552.html




 RSS Feed
RSS Feed
