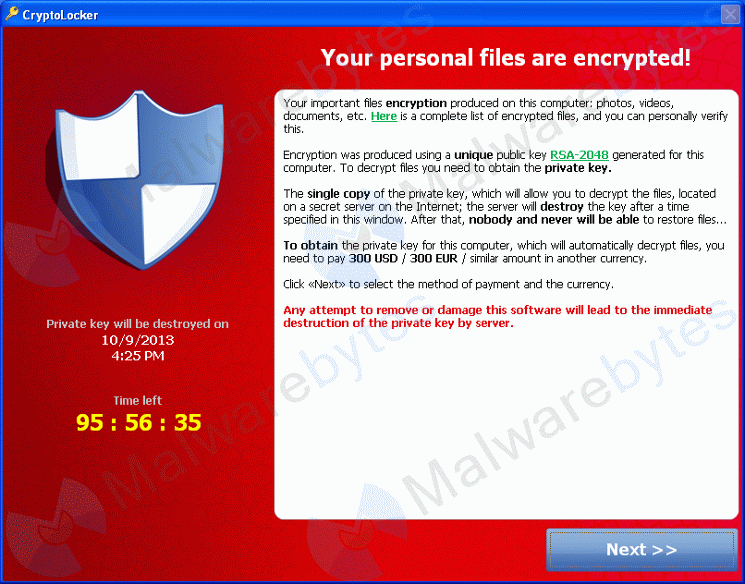
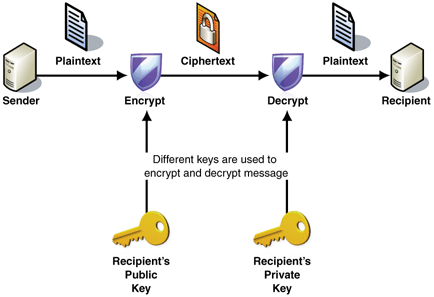
| Well, here I am once again to remind and caution you about the three most important things in computers and computing. Here they are (in descending order): 1) Backing up 2) Backing up 3) Backing up No seriously, while I have always been passionate in exhorting all my clients to establish and maintain a rigorous, reliable, and robust backup scheme, it is now even more critically important than ever. Although there have long been a broad and diverse array of threats and hazards to you, your computer, and your personal/business data "out there", among the ever-growing list of things against which to defend is now a chilling (relatively) new menace to your precious files, documents, photos, and other irreplaceable data - the CryptoLocker worm (and its analogues), or as it/they are also known in the industry, Ransomware. I have personally seen people who have been attacked and stricken by this insidious intruder, and the only ones who have come out totally (or at least mostly) unscathed were those who had relatively full and current backups of their critical data located on media off of (and physically disconnected from) their computers and from their home/office networks. What does it do, and how does it operate? Using a number of very clever, highly intelligent, and well-written algorithms it sends you zipped files (usually, but not necessarily always, PDF files) which appear to come from a trusted source such as your actual bank, phone company, internet service provider, and so on. These PDF files purport to be either a current bill, statement or other type of important customer information for your review. Once you've unzipped and opened the PDF file to look at it, your system has already become infected with the CryptoLocker worm (or one of its similar, new peers), which quickly - and amazingly efficiently - performs a thorough scan of all local and network shared drives, partitions, folders and even connected external media (such as your external backup hard disk), seeking out specific types of data and media files, and using strong (RSA public-key) cryptography protocols (with the private key held on their server) to encrypt (read: lock) your files, such that they can no longer be accessed by ANYONE (including you) without the private key. This cannot be decrypted - except maybe, and only maybe - by the Mossad, the CIA, or the NSA were they to apply their full computational decryption facilities to it, but, aside from the fact that they are never going to do this for you even if they could, and also due to the extreme strength and difficulty of brute force-breaking that would be required to "break" or decrypt your files, it is pretty much universally accepted and agreed that there is no feasible way to unlock them. They are lost to you forever - unless you have fairly thorough and recent backups of them, or (and hence the name, Ransomware) you are willing to pay a ransom (within a specified time limit) of anywhere from hundreds to thousands of dollars or euros to hopefully get the key from these hackers and regain access to your files. In other words, even though I have also often ardently and earnestly warned that ALL hard drives will fail - it is a question of when rather than if - with most typical scenarios of data loss or accidental/catastrophic deletion, you have a number of alternatives for attempting to recover your lost data (which may vary in cost anywhere from free to thousands of dollars, depending upon the physical/mechanical state of your Hard Drive / Storage Medium). However, in this Ransomware scenario, these nefarious operators can pretty much demand whatever price they want to return your data (access) to you, and not only do you have absolutely no other alternatives than those they offer - you don't even know for certain that you will, in fact, ultimately regain your access to the data in question - even after having submitted payment to them (I've seen more instances where they did indeed return the key, but others where, for whatever reasons, they decided to simply take the money and run, leaving you still without any access whatsoever to your data. How can you protect yourself and your data against these artfully treacherous attackers? Well, of course you can and should keep your system protected with a multi-layered protocol of security - including a (software or hardware) firewall, a good, robust antivirus program and at least one or two separate additional anti-malware/anti-spyware programs to help locate, identify, and remove the various and sundry little malevolent invaders which, in any case, are inevitably going intrude upon and occupy your computers, many of which - due to their lack of specific heuristic or definition/code signatures, may not be detected by your main antivirus program. But usually, by the time you've discovered that CryptoLocker or one its numerous analogues has invaded your computer, it is unfortunately probably too late for your data. You can easily find and remove the malware that encrypted your files, but as I elucidated above, you cannot remove the encryption from (nor regain access to) your files once they've been encrypted no matter what you do. So, the only real and true protection you can have against this very sophisticated and Machiavellian threat is to have a full, current and safely stored backup of ALL your important files - including but not necessarily limited to - documents, mail, contacts, spreadsheets, photos, PDFs, text and pretty much any other type of file formats that most of your commonly used productivity applications create and use. To sum up, I need to say, hear me now - and act to implement the necessary and appropriate protocols & procedures (security software and data backup), or take the considerable risk of being very sorry later on (perhaps even tomorrow or the next day?) Bleeping Computer on CryptoLocker MalwareBytes Security Blog / CryptoLocker Wikipedia on CryptoLocker The links above provide most, if not all, the information that is currently available regarding this phenomenon. Additionally, please feel free to contact me for consultation or advice on how best to proceed going about setting up the very best protection for your precious data and digital life that you can possibly provide. Beau - Israel's PC Doctor [email protected] 054-772-6239 (Israel Cell) +972-54-772-6239 (Cell from Out of Israel) +1-407-745-0882 (US Landline Rings at my Lab) Testimonials YouTube Video Testimonials |
|
0 Comments
 Even though Microsoft is withdrawing further support for Windows XP, they are still going to continue to allow anyone (and as of right now, this is fully 27.7% of the PCs out there) who still runs XP to download and install every single windows security, performance, and driver update they've ever issued. They will just not be building or issuing any new XP updates, so keeping your XP OS safely secured and stable will take just a bit of extra effort and initiative on your part. Here are some really good, useful techniques and tips for keeping your XP box up and running well and securely. Keep Your XP Alive, Well, & Running for Longer  Here are a whole bunch of very good useful tips to get your computer back up to its peak performance with a good, thorough (inside & out) Spring Cleaning. Definitely some very good advice.  Windows XP - It's been running, and running fairly well, for over a decade, but, as with most good things, it is finally coming to an end (together with Microsoft's Office 2003 suite). What are your options? Here's a good resource to see whether you (and your computer) are good candidates for upgrading to Windows 7, Windows 8, or a range of other possible solutions). http://www.howtogeek.com/172243/windows-xp-users-here-are-your-upgrade-options/  I can tell you, as a dedicated professional IT / Computer Support Tech/Consultant who works with this type of thing on virtually a daily basis, You Had Better Believe You Can!!!! If You Do Nothing Else For Your Own Data & Access Security, PLEASE READ THIS MESSAGE!!! Just a reminder to everyone who uses web-based email accounts such as Gmail, YahooMail, Hotmail, etc., we all know how complicated, unwieldy, and confusing it can managing all your various login authentication credentials (e.g.; user names & passwords), particularly since, these days, so many of us are using multiple email accounts - sometimes from a variety of providers, not to mention all the other programs, websites, and services (besides email) that we routinely or periodically need to remember how to access. Well, anyone who has seen any of my blogging will no doubt be aware of the numerous times that I've strongly advocated the use of one of the good password management programs that are fairly easily available (free & paid packages) online, such as LastPass or RoboForm. Ok, so let's say you've seen that and thought about doing that but haven't yet gotten around to it. This post isn't about chastising you for not taking adequate measures to ensure the security and accessibility of your valuable private data - I've done that enough already and will undoubtedly continue to do it in the future. What this communique is about is something that is even more basic and perhaps at least as important as your actual password management regime - and here it is: Making Absolutely Certain That All Your Alternate Contact Details (cell#, email, etc) Are Valid, Up-to-Date, and Still Accessible to You, & Perhaps Equally Important - Make Sure That You Know With Precise Accuracy What Your Security Questions (and of course, Their Answers) are, Including How They are Spelled, and Whether or Not They Include Upper/Lower Case Letters. For the vast majority of email & other web services you may use, as long as this information is valid, accurate, up-to-date, and you know exactly what it is (preferably have it written down somewhere), you will almost always be able to get an unlock / password reset key sent to you via your cell phone, alternate email address (it is crucial that you always have an active, alternate email account on record with your main email (or web site/service) provider for just this purpose). Because if you do not have any - or even enough of - the above items safely in place and accessible to you, and trust me, I've seen this happen far too many times, you CAN PERMANENTLY AND TOTALLY lose access to all your important, personal mail, contacts and whatever other files/data that you had stored there. And be warned that, in such cases, you can write to Gmail, Yahoo, or whomever - until the cows come home, if you do not have the information that they demand you provide in order to gain (re-gain) access to your account, they will not (according to them cannot) help you. That's it. Done. All your important correspondence, saved files, photos, contacts, calendar/schedule data - whatever you may have had on that site - could very well be GONE TO YOU FOREVER!!! Do I tell you this to scare you? You bet I do. No matter who you are and what you do, attempting to remember/replace/rebuild your lifetime's worth of important information is probably not something you look forward to having to deal with, and at least making sure that, if nothing else, you are able to prove to your account providers that you are actually you so that you can at least have them send you a password unlock or reset key, which could be all that stands between you and permanent, catastrophic data loss and account access loss. So what it boils down to is pretty much, at least at a bare minimum, if your site, web service or email account is important to you at all, make absolutely certain that you have the following in place: 1) current, accessible alternate contact details (phone,email, etc) 2) precisely known security questions and answers Having - or not having - those seemingly simple measures in place can make all the difference in the world to you on that dark day when you go to access your email, type in your password, and for some maddeningly unscrutable reason, it doesn't seem to work, and you face the dreaded "Access Denied" or "User Name / Password Combination Incorrect or not Found" message. Just sayin' better safe than sorry - especially when it is so easy to make sure that you - and your personal data/access are really safe and secure. Words to the wise . . . .  Do you have a business - a line of products or services that you are looking to promote and publicize? Keep in mind that if your business doesn't come up on the first page of the relevant search queries on Google, you're probably loosing a whole lot of visibility and therefore, of course, business and revenues. If you've recently upgraded to (or bought a new PC) Windows 8 and are wondering what in the world have they done with the handy old start menu where you used to access all your files and programs, they've done away with it, but you can download one that will integrate smoothly with your current Windows 8 installation and also give you the option to bypass the Metro start screen if you wish: http://download.cnet.com/StartMenu8/3000-2072_4-75852660.html?part=dl-&subj=dl&tag=button
 "...The Graph Search bar on Facebook has replaced my old search bar and now occupies a prominent place on the top tab of my Facebook homepage; the notifications, messages, friend requests tab are now on the right. The new design is giving Graph Search a lot more prominence and I’m not surprised, given Zuckerberg has called this the third pillar of the site at the launch . ." http://www.firstpost.com/tech/review-facebooks-graph-search-is-stalker-gold-605552.html  If you've been hearing all the buzz about Microsoft's new operating system, Windows 8 and are considering installing or upgrading to it, it is essential that you first verify that all your hardware and software are compatible with it. Otherwise you could run into major problems during the installation - you could even lose all your un-backed up personal or business data. There are a number of things you'll need to know, and I'll cover all of them here. |
AuthorHi there, I'm Beau - Israel's PC Doctor, and I created this new blog in order to try and help keep readers updated and in the know about things to do (or not do) and think about to enhance either their computers' performance, stability, security, productivity, or all of the above. 
Follow my Tech Support Facebook Page: http://tinyurl.com/PCdocFBfanPageWelcome
Archives
October 2014
Categories
All
|

 RSS Feed
RSS Feed
