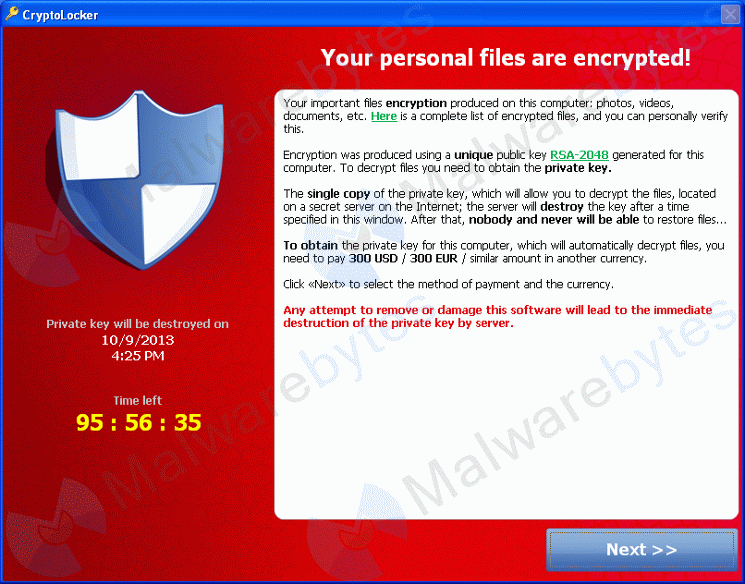
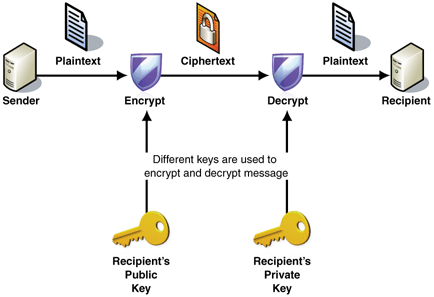
| Well, here I am once again to remind and caution you about the three most important things in computers and computing. Here they are (in descending order): 1) Backing up 2) Backing up 3) Backing up No seriously, while I have always been passionate in exhorting all my clients to establish and maintain a rigorous, reliable, and robust backup scheme, it is now even more critically important than ever. Although there have long been a broad and diverse array of threats and hazards to you, your computer, and your personal/business data "out there", among the ever-growing list of things against which to defend is now a chilling (relatively) new menace to your precious files, documents, photos, and other irreplaceable data - the CryptoLocker worm (and its analogues), or as it/they are also known in the industry, Ransomware. I have personally seen people who have been attacked and stricken by this insidious intruder, and the only ones who have come out totally (or at least mostly) unscathed were those who had relatively full and current backups of their critical data located on media off of (and physically disconnected from) their computers and from their home/office networks. What does it do, and how does it operate? Using a number of very clever, highly intelligent, and well-written algorithms it sends you zipped files (usually, but not necessarily always, PDF files) which appear to come from a trusted source such as your actual bank, phone company, internet service provider, and so on. These PDF files purport to be either a current bill, statement or other type of important customer information for your review. Once you've unzipped and opened the PDF file to look at it, your system has already become infected with the CryptoLocker worm (or one of its similar, new peers), which quickly - and amazingly efficiently - performs a thorough scan of all local and network shared drives, partitions, folders and even connected external media (such as your external backup hard disk), seeking out specific types of data and media files, and using strong (RSA public-key) cryptography protocols (with the private key held on their server) to encrypt (read: lock) your files, such that they can no longer be accessed by ANYONE (including you) without the private key. This cannot be decrypted - except maybe, and only maybe - by the Mossad, the CIA, or the NSA were they to apply their full computational decryption facilities to it, but, aside from the fact that they are never going to do this for you even if they could, and also due to the extreme strength and difficulty of brute force-breaking that would be required to "break" or decrypt your files, it is pretty much universally accepted and agreed that there is no feasible way to unlock them. They are lost to you forever - unless you have fairly thorough and recent backups of them, or (and hence the name, Ransomware) you are willing to pay a ransom (within a specified time limit) of anywhere from hundreds to thousands of dollars or euros to hopefully get the key from these hackers and regain access to your files. In other words, even though I have also often ardently and earnestly warned that ALL hard drives will fail - it is a question of when rather than if - with most typical scenarios of data loss or accidental/catastrophic deletion, you have a number of alternatives for attempting to recover your lost data (which may vary in cost anywhere from free to thousands of dollars, depending upon the physical/mechanical state of your Hard Drive / Storage Medium). However, in this Ransomware scenario, these nefarious operators can pretty much demand whatever price they want to return your data (access) to you, and not only do you have absolutely no other alternatives than those they offer - you don't even know for certain that you will, in fact, ultimately regain your access to the data in question - even after having submitted payment to them (I've seen more instances where they did indeed return the key, but others where, for whatever reasons, they decided to simply take the money and run, leaving you still without any access whatsoever to your data. How can you protect yourself and your data against these artfully treacherous attackers? Well, of course you can and should keep your system protected with a multi-layered protocol of security - including a (software or hardware) firewall, a good, robust antivirus program and at least one or two separate additional anti-malware/anti-spyware programs to help locate, identify, and remove the various and sundry little malevolent invaders which, in any case, are inevitably going intrude upon and occupy your computers, many of which - due to their lack of specific heuristic or definition/code signatures, may not be detected by your main antivirus program. But usually, by the time you've discovered that CryptoLocker or one its numerous analogues has invaded your computer, it is unfortunately probably too late for your data. You can easily find and remove the malware that encrypted your files, but as I elucidated above, you cannot remove the encryption from (nor regain access to) your files once they've been encrypted no matter what you do. So, the only real and true protection you can have against this very sophisticated and Machiavellian threat is to have a full, current and safely stored backup of ALL your important files - including but not necessarily limited to - documents, mail, contacts, spreadsheets, photos, PDFs, text and pretty much any other type of file formats that most of your commonly used productivity applications create and use. To sum up, I need to say, hear me now - and act to implement the necessary and appropriate protocols & procedures (security software and data backup), or take the considerable risk of being very sorry later on (perhaps even tomorrow or the next day?) Bleeping Computer on CryptoLocker MalwareBytes Security Blog / CryptoLocker Wikipedia on CryptoLocker The links above provide most, if not all, the information that is currently available regarding this phenomenon. Additionally, please feel free to contact me for consultation or advice on how best to proceed going about setting up the very best protection for your precious data and digital life that you can possibly provide. Beau - Israel's PC Doctor [email protected] 054-772-6239 (Israel Cell) +972-54-772-6239 (Cell from Out of Israel) +1-407-745-0882 (US Landline Rings at my Lab) Testimonials YouTube Video Testimonials |
|
0 Comments
 Even though Microsoft is withdrawing further support for Windows XP, they are still going to continue to allow anyone (and as of right now, this is fully 27.7% of the PCs out there) who still runs XP to download and install every single windows security, performance, and driver update they've ever issued. They will just not be building or issuing any new XP updates, so keeping your XP OS safely secured and stable will take just a bit of extra effort and initiative on your part. Here are some really good, useful techniques and tips for keeping your XP box up and running well and securely. Keep Your XP Alive, Well, & Running for Longer  Here are a whole bunch of very good useful tips to get your computer back up to its peak performance with a good, thorough (inside & out) Spring Cleaning. Definitely some very good advice.  Kerio (Free) Version for Home Users is widely known for its robust incoming and outgoing protection, while providing perhaps one of the most user-friendly, easy to configure and manage interfaces of offerings in its field (Firewall / Internet Security Apps). Here's a very good, thorough & informative review of its features and functions: http://www.melbpc.org.au/pcupdate/2304/2304article10.htm  Theft/Loss Insurance . . Despite all the various strategies we have discussed here recently regarding keeping your computer running cleanly, safely, & securely protected against a virtual panoply of existential threats, security breaches and malicious - often stealthy - intrusions, like the war that many governments constantly wage on terror, in order to remain free from damage or loss, we must be successful in defending against all the threats 100% of the time, but all the hackers, phishers, attackers need in order to be able to claim a significant degree of success in perpetrating their attacks against us can be as little as a single successful operation. But while we may or may not always succeed in perfectly protecting our precious, critical data and media from being soft targets for those who would lay claim to them (not to mention the plethora of other, technological or physical catastrophes that can occur on their own), we can at least take what can be considered essentially foolproof measures to avoid ending up having lost valuable, irreplaceable data due to the damage inflicted by viruses, worms, trojans, rootkits, hacktools, cyber-thieves, etc. - and this is by planning and implementing a conscientious and comprehensive program of backing up all the files, records, photos, music, videos, what have you, that we feel we cannot - or would prefer not to - live without. And those measures consist, in large part, of ensuring that our important data is regularly backed up to a second, inaccessible (to the malefactors) location. So backing up our data - exactly what that data comprises as well as precisely what we can do to ensure that we do it properly, reliably, and thoroughly - is what we are going to discuss next. Some of my Basic Backup Tips Here.  But even with all the aforementioned security and maintenance measures we've discussed here in this blog, for a variety of reasons, some of you may still feel a need to ratchet your security scenarios up a level or two. If this is you, then you are probably a candidate for a Personal Firewall software application. Here is a decent comparison shopping review of some of the best, most popular Firewall applications on the market: http://personal-firewall-software-review.toptenreviews.com/ Several of them do offer, less than fully featured, but still useful, free versions for non-business use.  Further to my previous posting regarding the cleaning, purging, exfoliating, debridement, and sanitizing of your computer's operating system, sometimes, at various points along the way in that process, you may come upon files or folders that you want to delete but are told you do not have access or authority to delete them. This can be aggravating, but don't worry! Just download and install Unlocker 64bit (http://download.cnet.com/Unlocker-64-bit/3000-2094_4-11893280.html) or the 32bit version if that is the type of operating system you've got: (http://www.softpedia.com/get/System/System-Miscellaneous/Unlocker.shtml). With Unlocker, you can regain control over the files in your own computer and delete just about whatever you might want to delete - without needing anybody's (or anything's) authorization or consent, which you would not likely receive in any case. |
AuthorHi there, I'm Beau - Israel's PC Doctor, and I created this new blog in order to try and help keep readers updated and in the know about things to do (or not do) and think about to enhance either their computers' performance, stability, security, productivity, or all of the above. 
Follow my Tech Support Facebook Page: http://tinyurl.com/PCdocFBfanPageWelcome
Archives
October 2014
Categories
All
|

 RSS Feed
RSS Feed
